During an investigation of a large PE file, analysis tools identified that a significant part of the file was made up of an “overlay”. I could not find a lot of information about overlays so I researched and have documented my findings here.
What is an overlay?
In simple terms, an overlay is additional data added to the end of a PE file. Many common PE analysis tools will show the presence of an overlay and provide varying levels of detail.
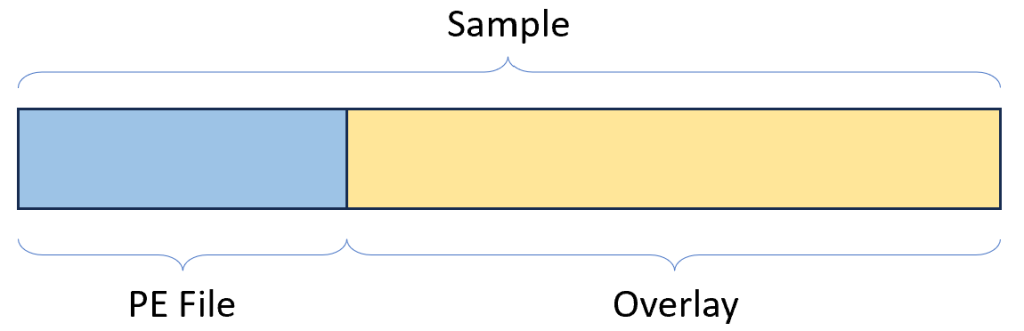
The PE section of the sample is a complete executable. However when the file is loaded into memory the overlay is not mapped.
Analysis
The sample analysed was obtained from VirusTotal:
1000f3f1280e5b2998c5c1550077779542372201ceaff72ee74cdd4d04f72940
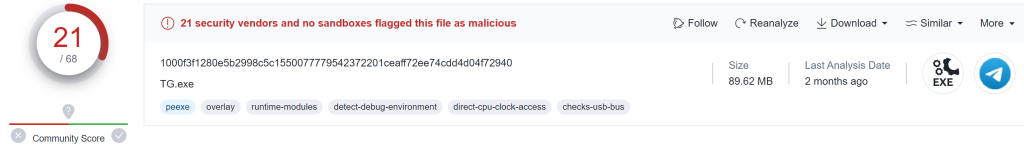
The file is 89.62 MB and has been identified as a PE32 executable. We can also see that the file has been identified as malicious by several vendors (21/68 at time of writing). Opening the file in DiE (Detect it Easy) the presence of an overlay can be seen (red arrow)

DiE has detected the the overlay is also itself a PE file and the green arrow shows that the overlay also contains an overlay. Things are starting to get a little Inception!
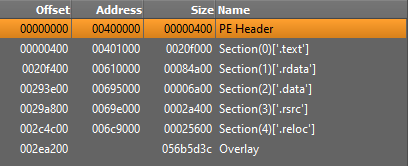
Looking at the memory map section we see from the size column that the Overlay section is the largest. The Address column shows the address in memory that the various sections would be mapped to. Note no entry for the Overlay section meaning it does not get mapped into memory.
If we select the overlay section we can see the hex dump at that memory location and it shows MZ, the start of a DOS header. This agrees with the automated analysis shown above.
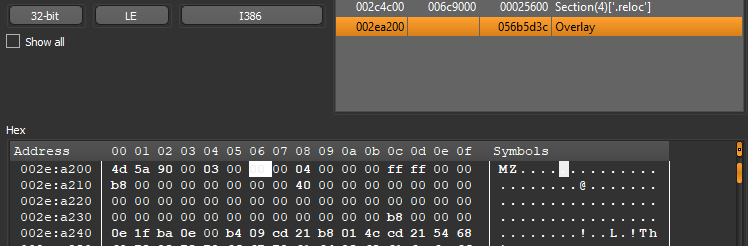
We can dump the overlay section and save to disk…
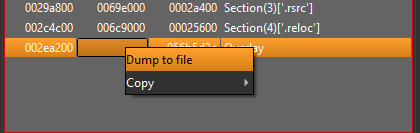
Analysing the dumped file in DiE we can see the this file does contain an overlay. It also shows the the PE32 at the start of of this dumped file is a DLL – see red box below.
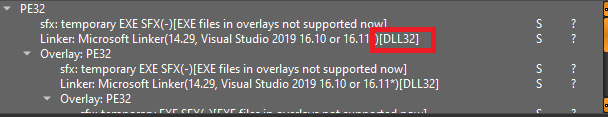
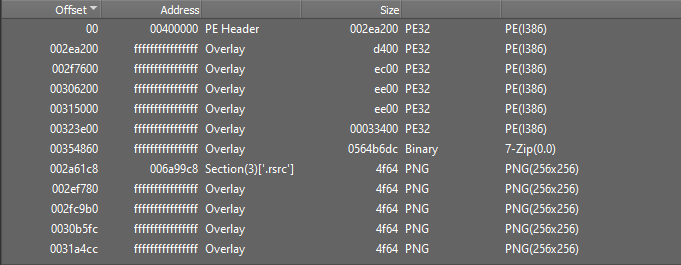
If this process is continued it will be seen that apart from the original PE32 executable file at the start of the original sample there are 5 DLL files contained in layered overlay sections and a final section identified as “binary” data.
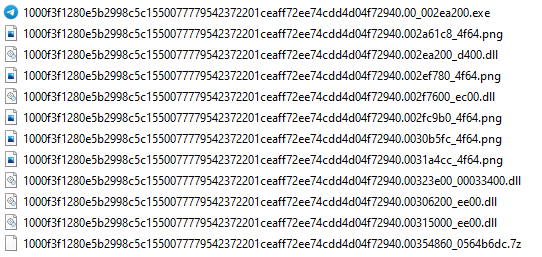
DiE includes an Extractor facility which allows all files to be extracted and dumped to disk in a single step. The result is shown below. The binary data section has been extracted as a 7-Zip file. The format of the naming for the extracted files is:
<SHA256 hash of original sample>.<offset>_<size>.<extension>
| File (offset) | SHA256 | VT Score |
| 00 | 257b15fd51f056f2f5be8a580d7cfc40850310fd9dfefd8078b9e37336da1126 | 1/70 |
| 002a61c8 | a1443d68e263069da2f397dc56c886d4b8279de986ff068ece4488cc5c085bb0 | 0/70 |
| 002ea200 | 5ffff4590ff56fbb7edf5537e57b72d29fb1cd353f62c7cef15cea73b292b335 | 0/70 |
| 002ef780 | a1443d68e263069da2f397dc56c886d4b8279de986ff068ece4488cc5c085bb0 | 0/70 |
| 002f7600 | b90bfb7e6d3a41b04940c323d12896660107f432e536aa6783d57f7d7a2459f0 | n/a |
| 002fc9b0 | a1443d68e263069da2f397dc56c886d4b8279de986ff068ece4488cc5c085bb0 | 0/70 |
| 00306200 | 3a1cf719eef260d92924790b34a6b206e79e72f4d10fd192aa47943d39bf6334 | n/a |
| 0030b5fc | a1443d68e263069da2f397dc56c886d4b8279de986ff068ece4488cc5c085bb0 | 0/70 |
| 00315000 | e21da2260d39fc919af3731256277652d3bfc9620ebc4046016ce341a546763e | n/a |
| 0031a4cc | a1443d68e263069da2f397dc56c886d4b8279de986ff068ece4488cc5c085bb0 | 0/70 |
| 00323e00 | d4282c9805e7ff97a7bebcbbed608d7daa3dc4c72354690ba94b685550728549 | 0/70 |
| 00354860 | 7bf45759e510c502e3b4f132c35252c3ed16ad03776f92c8bde66b7b98c2c55d | 0/70 |
Conclusion
Using basic analysis tools we can see and extract complex multi-layered overlay structures. The sample examined here appears to show a suspicious PE executable file with low detection (1/70) and 5 DLL files embedded in the overlay. It is likely that the DLL files are included to support the operation of the executable.
The purpose of the large binary file is not known at this time. It is not a 7-Zip file and does not deflate. My hope is to return to this and add a supplementary blog at some stage.
David